VPC’s Architecture and its components

VPC Architecture diagram
VPC comprises various components
Internet Gateway:
- An Internet Gateway (IGW) is a logical connection between an Amazon VPC and the Internet.
- It is not a physical device and Only one can be associated with each VPC.
- When we create IGW, it will not be attached to the VPC automatically, we need to explicitly attach it to the VPC.
- If a VPC does not have an Internet Gateway, then the resources in the VPC cannot be accessed from the Internet.
- It does not limit the bandwidth of Internet connectivity. (The only limitation on bandwidth is the size of the Amazon EC2 instance, and it applies to all traffic — internal to the VPC and out to the Internet.)
AWS Router: Each AWS VPC has a VPC router.
The primary function of this VPC router is to take all of the route tables defined within that VPC and then direct the traffic flow within that VPC, as well as to subnets outside of the VPC, based on the rules defined within those tables.
Route Table and how does it work?
- A set of rules, called routes, are used to determine where network traffic is directed.
- A route table is used to determine where network traffic from your subnet or gateway is directed. In simple terms, the route table tells network packets which way they need to go to get to their destination.
- A subnet can only be associated with one route table at a time, but you can associate multiple subnets with the same subnet route table.
- Every route table contains a local route for communication within the VPC. This route is added by default to all route tables.
Main Route Table:
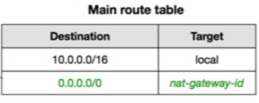
Main route table
The first entry is the default entry for local routing in the VPC.
- This entry enables the instances in the VPC to communicate with each other over IPv4.
- The second entry routes all other IPv4 subnet traffic from the private subnet to your network over the virtual Nat gateway (for example,
nat-1a2b3c4d) - The Main route table automatically comes with your VPC that is used by default for any subnet that isn’t explicitly associated with a routing table.
Custom Route Table:
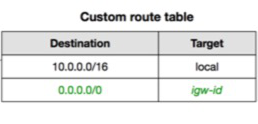
Custom route table
Custom route table that you create for your VPC.
- The first entry is the default entry for local routing in the VPC.
- This entry enables the instances in the VPC to communicate with each other.
- The second entry routes all other IPv4 subnet traffic from the public subnet to the internet over the internet gateway (for example,
igw-1a2b3c4d
The Destination is the pattern for where the packet is trying to end up and the Target is where the packet should go. For example, packets with a destination within 10.0.0.0/16 should be routed directly inside the VPC.
In the above VPC architecture, we have defined public and private route tables so let’s understand it.
Public Route Table — Routing to Internet Gateway: The route table which is directly associated with the Internet gateway is called the Public Route table. To make the route table public, we need to add routes destination 0.0.0.0 and Target the Internet Gateway id.

Private Route Table — Routing to Nat Gateway: The route table which is directly associated with the Nat gateway is called the Private Route table. To make the route table private, we need to add routes destination 0.0.0.0 and Target the Nat Gateway id.
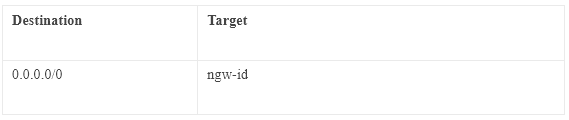
Nat Gateway:
- NAT device enables instances in a private subnet to connect to the Internet or other AWS services but prevents the Internet from initiating connections with the instances.
- NAT gateway always resides inside the public subnet of an Availability Zone.
- Elastic IP must be attached to the NAT gateway while creating.
- NAT devices do not support IPv6 traffic, use an egress-only Internet gateway instead.
Subnet:
- A subnet is a range of IP addresses in your VPC and it is a logical subdivision of the VPC network.
- The practice of dividing a network into two or more networks is called subnetting.
- AWS provides two types of subnetting one is Public which allows the internet to access the machine and another is private which is hidden from the internet.
- A subnet is a span to a single availability zone.
Public Subnet:
- A public subnet is a subnet that’s associated with a route table (public route table) that has a route to an internet gateway.
- Resources that reside within the public subnet can access the Internet with an Internet gateway.
Private Subnet:
- A public subnet is a subnet that’s associated with a route table (private route table) that has a route to a NAT gateway.
- Resources that reside within the private subnet can access the Internet with a NAT gateway.
- The resources from private subnet such as Mysql DB, private VM can’t be accessed directly from the internet.
- We can use VPN as a service from AWS or can a bastion host in the public subnet to connect the resources in the private subnet.
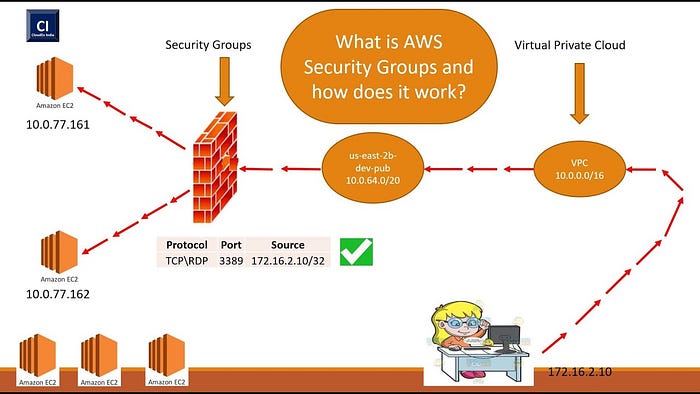
VPC Security
Security within a VPC is provided through
Security groups :

- Acts at an Instance level firewall but not at the subnet level.
- Each instance within a subnet can be assigned a different set of Security groups
- Default Security Group allows all outbound traffic
- In the Security group, we can specify only Allow rules, but not deny rules.
- Security Groups are Stateful — If a request is allowed, the response for the request is automatically allowed.
Network access control lists (ACLs):
- It is a security layer for your VPC which is applied on the subnet level.
- stateless firewall — you need to allow both inbound and outbound traffic.
- It is an optional layer for your VPC and can set up a Network ACL similar to the security group that adds an additional layer of security to your VPC.
- When you create VPC, it creates default Network ACL automatically which includes all inbound and outbound ipv4 traffic.
- You can also create a custom network ACL and associates it with a subnet. By default, a custom Network ACL denies all the inbound and outbound ipv4 traffic until you add rules.
- Act as a firewall for associated subnets, controlling both inbound and outbound traffic at the subnet level
Flow logs:
- VPC Flow Logs is a feature that enables you to capture information about the IP traffic going to and from network interfaces in the VPC and can help in monitoring the traffic or troubleshooting any connectivity issues.
- Flow log data is stored using Amazon CloudWatch Logs.
- Flow log can be created for the entire VPC, subnets, or each network interface. If enabled, for the entire VPC or subnet all the network interfaces are monitored
- Flow logs do not capture real-time log streams for network interfaces.
IP Addresses
Instances launched in the VPC can have Private, Public, and Elastic IP address assigned to them.
Private IP Addresses:
- Private IP addresses are not reachable over the Internet and can be used for communication only between the instances within the VPC
- All instances are assigned a private IP address, within the IP address range of the subnet, to the default network interface
- The private IP address is associated with the network interface for its lifetime, even when the instance is stopped and restarted and is released only when the instance is terminated
- Additional Private IP addresses, known as secondary private IP address, can be assigned to the instances and these can be reassigned from one network interface to another
Public IP address:
- Public IP addresses are reachable over the Internet and can be used for communication between instances and the Internet.
- The public IP address assigned to the Instance depends if the Public IP Addressing is enabled for the Subnet.
- The public IP address can also be assigned to the Instance by enabling the Public IP addressing during the creation of the instance.
- The public IP address is assigned from the AWS pool of IP addresses and it is not associated with the AWS account and hence is released when the instance is stopped and restarted or terminated.
Elastic IP address:
- Elastic IP addresses are static, persistent public IP addresses that can be associated and disassociated with the instance, as required.
- The elastic IP address is allocated at a VPC and owned by the account unless released.
- A Network Interface can be assigned either a Public IP or an Elastic IP. If you assign an instance, already having a Public IP, an Elastic IP, the public IP is released.
- Elastic IP addresses can be moved from one instance to another, which can be within the same or different VPC within the same account
- Elastic IP is charged for non-usage i.e. if it is not associated or associated with a stopped instance or an unattached Network Interface